Log into JUMPBOX VM (172.16.10.10) and configure it as a repository by running the following commands as root.
# yum install –y open-vm-tools net-tools wget bridge-utils tftp tftp-server \ dhcp httpd php gd php-gd syslinux epel-release # vi /etc/selinux/config ----- SELINUX=disabled ----- # systemctl stop firewalld.service # systemctl disable firewalld.service # yum –y update ; sync ; sync ; reboot
- Download SUSE CaaSP 2.0 Platform from SUSE web site
- Upload the iso image to local Datastore
- Connect it to CDROM of JUMPBOX VM
- Power on the VM
- I logged in as a regular user (named ‘student’) and then ran ‘su – root’
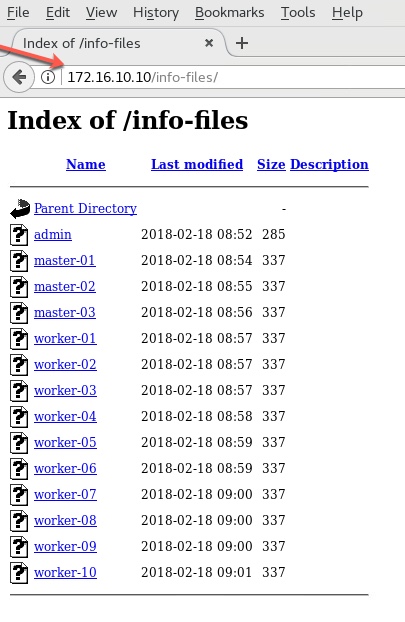
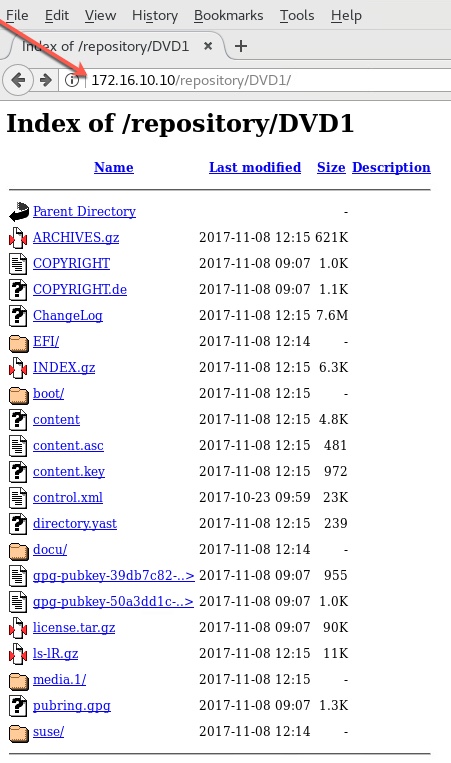
# cd /var/www/html # mkdir -p repository/DVD1 # mkdir info-files # cd repository/DVD1 # cp -rav /run/media/student/SUSE-CaaS-Platform-2.0-DVD-86_6/* ./repository/DVD1 # chmod -R 755 * # chown -R apache:apache *
- Create a file to define an alias for /repository.
- The filename can be anything, as long as it it located in directory /etc/httpd/conf.d
# vi /etc/httpd/conf.d/pxeboot.conf ----- Alias /repository /var/www/html/repository <Directory /var/www/html/repository> Options Indexes FollowSymLinks Allow from all </Directory> -----
- Modify httpd.conf
# vi /etc/httpd/conf/httpd.conf ----- Listen 172.16.10.10:80 ServerName jumpbox.susecaas.local:80 -----
- Define ‘info-files’ for each virtual machine, starting with ADMIN (node) VM
# cd /var/www/html/info-files # vi admin ----- netdevice=eth0 ifcfg="eth0=172.16.10.50/24,172.16.10.253,172.16.10.250,susecaas.local" hostip=172.16.10.50/24 netmask=255.255.255.0 gateway=172.16.10.253 nameserver=172.16.10.250 domain=susecaas.local hostname=admin.susecaas.local install=http://jumpbox.susecaas.local/repository/DVD1 -----
- Define info-file for MASTER-01 VM
# vi master-01
-----
netdevice=eth0 ifcfg="eth0=172.16.10.101/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.101/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=master-01.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
-----
- Define info-file for MASTER-02 VM
# vi master-02
-----
netdevice=eth0 ifcfg="eth0=172.16.10.102/24, 172.16.10.253, 172.16.10.250,susecaas.local"
hostip=172.16.10.102/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=master-02.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
-----
- Define info-file for MASTER-03 VM
# vi master-03
-----
netdevice=eth0 ifcfg="eth0=172.16.10.103/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.103/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=master-03.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-01 VM
# vi worker-01
-----
netdevice=eth0 ifcfg="eth0=172.16.10.201/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.201/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-01.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-02 VM
# vi worker-02
-----
netdevice=eth0 ifcfg="eth0=172.16.10.202/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.202/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-02.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-03 VM
# vi worker-03
-----
netdevice=eth0 ifcfg="eth0=172.16.10.203/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.203/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-03.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-04 VM
# vi worker-04
-----
netdevice=eth0 ifcfg="eth0=172.16.10.204/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.204/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-04.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-05 VM
# vi worker-05
-----
netdevice=eth0 ifcfg="eth0=172.16.10.205/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.205/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-05.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-06 VM
# vi worker-06
-----
netdevice=eth0 ifcfg="eth0=172.16.10.206/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.206/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-06.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-07 VM
# vi worker-07
-----
netdevice=eth0 ifcfg="eth0=172.16.10.207/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.207/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-07.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-08 VM
# vi worker-08
-----
netdevice=eth0 ifcfg="eth0=172.16.10.208/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.208/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-08.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-09 VM
# vi worker-09
-----
netdevice=eth0 ifcfg="eth0=172.16.10.209/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.209/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-09.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
----
- Define info-file for WORKER-10 VM
# vi worker-10
-----
netdevice=eth0 ifcfg="eth0=172.16.10.210/24,172.16.10.253,172.16.10.250,susecaas.local"
hostip=172.16.10.210/24
netmask=255.255.255.0
gateway=172.16.10.253
nameserver=172.16.10.250
domain=susecaas.local
hostname=worker-10.susecaas.local
install=http://jumpbox.susecaas.local/repository/DVD1
autoyast=http://admin.susecaas.local/autoyast
-----
- Charge ownership of all info-files to the web server
# pwd
/var/www/html/info-files
# chmod 755 *
# chown apache:apache *
- Start the web server
# systemctl start httpd.service
# systemctl enable httpd.service
# systemctl status -l httpd.service
Now open up the browser in the JUMPBOX VM itself and verify that the files in directories namely
/var/www/html/repository/DVD1 and /var/www/html/info-files are accessible from the browser.
This confirm that the website is now completed successfully as a repository.